The digital Guard Dog
for your websites
Identified web vulnerabilities in one dashboard, with prioritisation, follow-up and audit-ready evidence.
We run 40+ security checks daily across your domains.
Trusted by developers, governments and enterprises



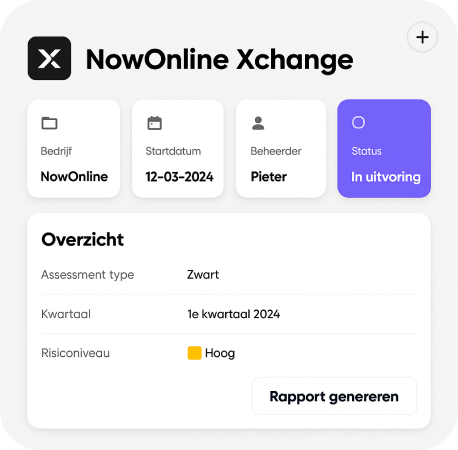
Don’t waste your security budget on manual work.
Sound familiar? Someone runs a scan from time to time, receives a report that no one really uses, and when an audit comes around, a stressful search begins for what was actually done. Meanwhile, new vulnerabilities emerge every day, you’re working with multiple tools, ad-hoc alerts and spreadsheets and your best people are spending time on copy-paste tasks and manual logging.
In short: for serious compliance, this approach doesn’t scale, wastes talent, and consumes a lot of time while delivering very little control.
How the Security Monitor works
Security Monitor is your daily vulnerability monitor for all websites across your organisation, giving you clear insight into detected vulnerabilities and the actions needed to address them.
- We run 40+ independent scans daily
- We analyse and categorise the results
- We translate findings into concrete, prioritised actions
- You get one clear overview of what is urgent and what has already been resolved
- We retain the full history as audit-ready evidence

Speed and scalability in Security & Compliance
From risk to evidence: demonstrably compliant in three steps
40+ sources, one overview
Daily insight
Demonstrably in control
Save time, effort and proof
Your team stays in control while we keep the repetitive scanning work running.
For Security Teams
- Clear to-do items per domain
- Priorities immediately visible
- Fewer ad-hoc requests across different channels
- One dashboard with a clear overview of which issues belong to which vendor or internal team
For IT Teams
- Always an up-to-date view of external vulnerabilities
- Easy handover of signals and findings (email)
- One prioritised backlog instead of separate reports
- Direct input for Risk & Compliance and senior management
Digital Guard Dog:
active in 3 simple steps
1
Start a free scan
We immediately connect your websites to our 40+ sources and run your first checks.
2
Initial findings within minutes
You get access to the dashboard and can see at a glance where action is required and what can wait.
3
First full report within 24 hours
All identified vulnerabilities are available in the dashboard, including their impact and the ability to forward them directly to colleagues or external parties.
Like what you see?
With one click, you switch to daily monitoring with alerts, signal tracking, and a complete audit trail.
Activate your digital Guard Dog!
The key features that deliver immediate value:
40+ security checks
Combine internet standards, DNS, email, TLS/SSL, blacklists, and much more across multiple domains in a single overview.
No separate scans, manual work, or in-house tooling required.
Categorised output
Results from different scans are combined, deduplicated, categorised, and normalised.
Each vulnerability is always confirmed by two independent sources.
Daily monitoring
Based on new scan results, you automatically see whether an issue has been resolved.
Receive new vulnerabilities every day and not just at the annual audit.
Issue tracker & workflow
Turn vulnerabilities into tasks, assign them, set priorities, and track their status.
Perfect for collaboration between security, IT, and third parties.
Audit-trail
Export with one click what was identified, addressed, and resolved.
Ideal for audits, assessments, and discussions with regulators and executive management.
Ready for your stack
Use Security Monitor as a standalone dashboard or integrate it with your existing ticketing or SOC processes.
Your workflow stays the same with better input.

Compliance is about evidence
Whichever standard you follow — NIS2, ISO 27001, NEN 7510, BIO, or GDPR – you must be able to demonstrate that vulnerabilities are identified, assessed, and addressed in a timely manner.
- Technical vulnerability management embedded
Daily scans prove that you operate a continuous process rather than relying on one-off or ad-hoc checks. - Demonstrably in control
The audit trail shows which vulnerabilities were found, assessed, and resolved and when. - Easy to explain to boards and auditors
One dashboard with all the information: how often you scan, what you find, and how you act.
Demonstrably in control with the Security Monitor
Monthly or annual licence
Receive one month free with a 1-year licence.
Security Monitor
Perfect voor aantoonbare compliance
-
Meerdere domeinen in één dashboard
-
Signalen in applicatie
-
Kwetsbaarheden beheer
Security Monitor
Perfect voor aantoonbare compliance.
-
Dagelijkse scan
-
Meerdere websites in één Dashboard
-
Dagelijks rapportage via de mail
-
Signalen in Applicatie
-
Kwetsbaarheden beheer
“Lorem ipsum dolor sit amet, consectetur adipiscing elit. Sed do eiusmod tempor …”
Anna lorenz
“Lorem ipsum dolor sit amet, consectetur adipiscing elit. Sed do eiusmod tempor …”
Anna lorenz
“Lorem ipsum dolor sit amet, consectetur adipiscing elit. Sed do eiusmod tempor …”
Anna lorenz
“Lorem ipsum dolor sit amet, consectetur adipiscing elit. Sed do eiusmod tempor …”
Anna lorenz
“Lorem ipsum dolor sit amet, consectetur adipiscing elit. Sed do eiusmod tempor …”
Anna lorenz
“Lorem ipsum dolor sit amet, consectetur adipiscing elit. Sed do eiusmod tempor …”
Anna lorenz
“Lorem ipsum dolor sit amet, consectetur adipiscing elit. Sed do eiusmod tempor …”
Anna lorenz
“Lorem ipsum dolor sit amet, consectetur adipiscing elit. Sed do eiusmod tempor …”
Anna lorenz
“We’re a developer and sold our first phase in 3 months thanks to Domino”
Alejandro Gutiérrez
“Lorem ipsum dolor sit amet, consectetur adipiscing elit. Sed do eiusmod tempor …”
Anna lorenz
“Lorem ipsum dolor sit amet, consectetur adipiscing elit. Sed do eiusmod tempor …”
Anna lorenz
“Lorem ipsum dolor sit amet, consectetur adipiscing elit. Sed do eiusmod tempor …”
Anna lorenz
1450+ mensen geholpen
Deze mensen
waren je voor!
Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum.
Frequently Asked Questions
Does Security Monitor replace our pentests?
No. Pentests remain essential for in-depth, creative testing. Security Monitor complements pentests by providing daily, automated monitoring of known and emerging vulnerabilities, so you’re never in the dark between pentest cycles and always maintain visibility into your risks.
Can’t we just build this ourselves?
In theory: yes. In practice: You would need a team to maintain 40+ sources, write and maintain scripts and logic, connect data, build and manage dashboards, and log everything properly. With Security Monitor, you get this entire layer ready-to-use.
How can we get started?
Start with a free scan. We immediately connect your websites to our 40+ sources and run your first checks.
How quickly will we see results?
Within minutes, the first findings appear in your dashboard.
Within 24 hours, you receive a complete report with prioritized vulnerabilities and recommendations.
What about our data and security?
We only scan what is publicly available. Reports and logs are visible only to your authorized users. Results are never shared without your consent, and all data is securely processed and stored on Western European servers.
Do we need a SOC or a large team?
No. Both small and large teams can use Security Monitor. Use it as a standalone dashboard or as a signal source for your SOC or ticketing system.
Security Monitor gives your team time, convenience, and proof without manual scanning work.